Secure mobile phone for professional users with 360° protection, hardened operating system, Baseband Firewall, tamper-resistant hardware and end-to-end voice and message encryption
Secure CallsGSMK CryptoPhone 600G Secure Mobile
Secure end-to-end encrypted voice over IP calls on any network – 2G, 3G, 4G, WLAN
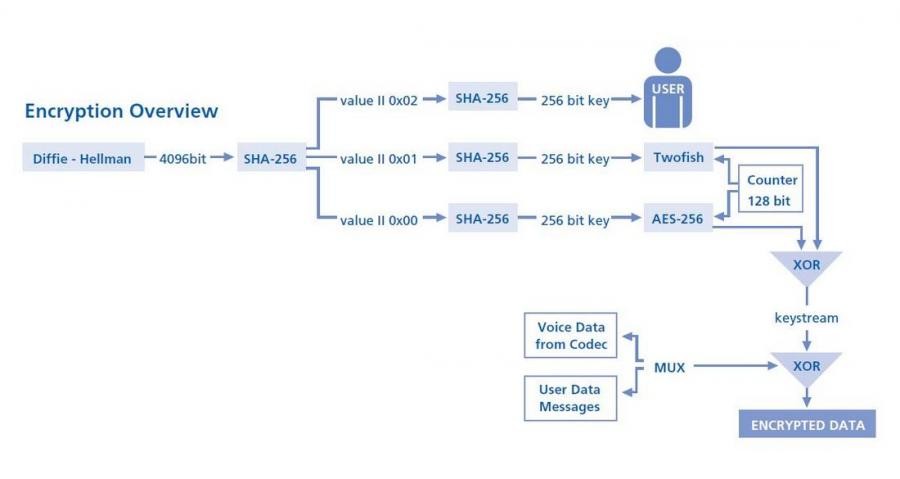
Strongest and most secure algorithms available today – AES256 and Twofish
4096 bit Diffie-Hellman key exchange with SHA-256 hash function
Readout-hash based key authentication
Autonomous key generation, no pre-installed key material
Encryption keys securely and immediately erased from the device after each call
Secure Messaging
Based on the same strong encryption algorithms used for GSMK CryptoPhone voice encryption – 4096 bit Diffie-Hellman initial key exchange, AES256 and Twofish message encryption with 256 bit keys
More information on:
GSMK Crypto Phone 600G
Secure CallsGSMK CryptoPhone 600G Secure Mobile
Secure end-to-end encrypted voice over IP calls on any network – 2G, 3G, 4G, WLAN
Strongest and most secure algorithms available today – AES256 and Twofish
4096 bit Diffie-Hellman key exchange with SHA-256 hash function
Readout-hash based key authentication
Autonomous key generation, no pre-installed key material
Encryption keys securely and immediately erased from the device after each call
Secure Messaging
Based on the same strong encryption algorithms used for GSMK CryptoPhone voice encryption – 4096 bit Diffie-Hellman initial key exchange, AES256 and Twofish message encryption with 256 bit keys

More information on:
GSMK Crypto Phone 600G
